Web Security Model Problem
One of the main problems with the current security model on the web is that the problem is not someone stealing the password in transit...but as you type it in. Spyware has got so complex nowadays that they can even take screengrabs of the places where drop down boxes instruct you to enter a few chars of your password as a secondary measure (e.g. LloydsTSB).
One of the ways round could be to do what some of the banks are doing and sending dongles to their customers which means that the customer has to carry round with him something physical and therefore it is not only inconvenient but there is a chance of losing the device resulting in lockout.
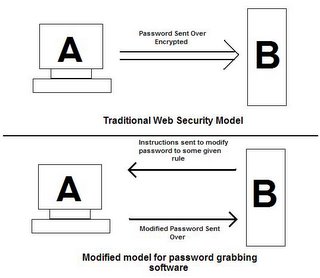
One method that I think could be effective against the advanced spyware (keyloggers, screengrabbers) is by getting the banks to actually send some sort of "instruction" that gets the user to send a modified password across. This would mean that the password entered would be different each time and that by just getting the password alone the phishers would not be able to make use of it. For example, an instruction could consist of reversing the password or entering the first three characters at the end. The main idea here is that the computation must be able to be done in the customers head without too much thought. This could therefore be something like "please add the day to the end of your password" just so that it is something that changes on a regular basis.
Another method would be to register each computer that you wish to access the bank account with. This would only work in cases where the person uses very few computers (e.g. home and work). It would need to be quite flexible in terms of IP since users at home will most likely have a dynamic IP address and so a slightly larger range would have to be accommodated.
Even easier would be to get Microsoft to make keylogging, screengrabbing, etc require higher privileges and so only performable with entering in the password.
One of the ways round could be to do what some of the banks are doing and sending dongles to their customers which means that the customer has to carry round with him something physical and therefore it is not only inconvenient but there is a chance of losing the device resulting in lockout.
One method that I think could be effective against the advanced spyware (keyloggers, screengrabbers) is by getting the banks to actually send some sort of "instruction" that gets the user to send a modified password across. This would mean that the password entered would be different each time and that by just getting the password alone the phishers would not be able to make use of it. For example, an instruction could consist of reversing the password or entering the first three characters at the end. The main idea here is that the computation must be able to be done in the customers head without too much thought. This could therefore be something like "please add the day to the end of your password" just so that it is something that changes on a regular basis.

Another method would be to register each computer that you wish to access the bank account with. This would only work in cases where the person uses very few computers (e.g. home and work). It would need to be quite flexible in terms of IP since users at home will most likely have a dynamic IP address and so a slightly larger range would have to be accommodated.
Even easier would be to get Microsoft to make keylogging, screengrabbing, etc require higher privileges and so only performable with entering in the password.

0 Comments:
Post a Comment
<< Home